Authenticated API
This page describes how to connect your application to an API with authentication.
Use this datasource to create multiple queries for the same API. Every query created from this datasource has shared configuration (root URL, authentication, headers, and so on) to avoid re-entering details. If you're only creating a single query for your API, try using a REST API datasource.
Connection parameters
The following section is a reference guide that provides a complete description of all the parameters available for REST APIs.
The datasource configuration fields do not accept JavaScript code or mustache syntax.
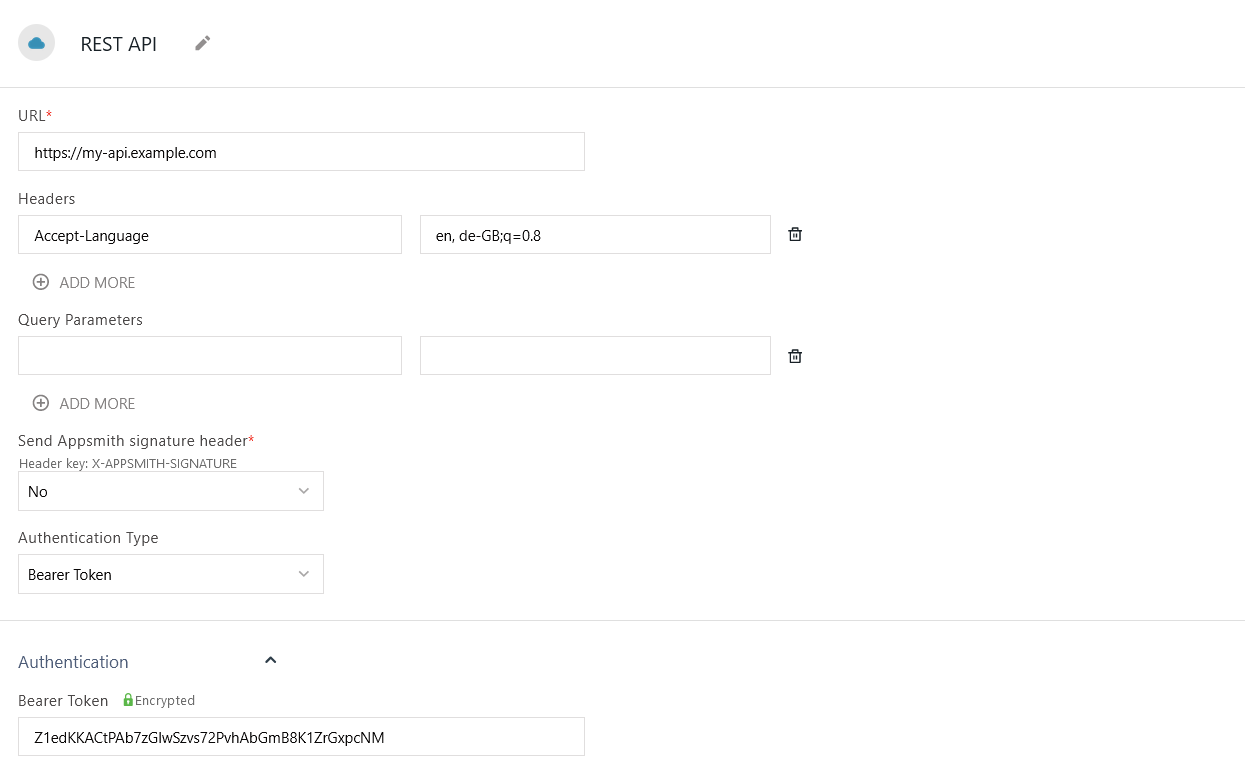
URL
The URL of the service to query. For a guide about connecting to a local APIs, see Connect Local Database.
Headers
Key-value pairs to include in the header section of your HTTP requests.
Query parameters
Key-value pairs that should be passed as parameters in the URL of your HTTP requests.
Send Appsmith signature header
When enabled, you can enter a secret string of at least 32 characters in the Session Details Signature Key field. Every API call made to this datasource then includes an additional header, X-Appsmith-Signature, whose value is a JSON Web Token (JWT) signed with a signature created from your secret string. This can be used to help prove the integrity and authenticity of your requests originating from Appsmith.
Authentication Type
- None: Does not send any authentication information.
- Basic: Expects a Username and Password, which are sent in each request as a base64-encoded string in the request's Authorization header.
- OAuth 2.0: Enables several fields for configuring an OAuth 2.0 integration.
- Grant Type: An authorization grant type is a secured representation of the owner’s authorization presented in exchange for an access token. Options:
- Authorization Code : An authorization code is a temporary code authorized by an authorization server. You can get an access token in exchange for an authorization code. Once you get an access token, you can use it to access the resources or perform actions on behalf of the user.
- Client Credentials.
- Add Access Token To: Sets whether the access token is sent as a Request Header or as a query parameter (Request URL).
- Header Prefix: When the access token is sent as a header, this sets a string to prefix the access token. A common example is
Bearer. - Access Token URL: The endpoint on the authentication server that is used to exchange the authorization code for an access token.
- Client ID: The identifier issued to the client by the OAuth provider during app registration.
- Client Secret: The secret string issued to the client by the OAuth provider during app registration.
- Scopes: Sets the requested scopes that are requested. This field can have multiple comma-separated values.
- Client Authorization: Sends the client secret either in the request body as
client_idandclient_secretparameters or within the headers encoded as basic HTTP authentication. - Authorization URL: The endpoint on the authentication server that is used to request authentication for the client.
- Redirect URL: The URL that the OAuth server should redirect to.
- Custom Authentication Parameters: User-defined key/value pairs to be encoded and sent as authentication parameters.
- Audience: Expects a URL, specifies the intended audience for the OAuth access token.
- Resource: Expects a URL, specifies an application to act as a resource server.
- API Key: Sends a key/value pair which is sent as a base64-encoded string in the request's Authorization header. You can specify the key's prefix, as well as choose whether it's sent in the request header or the query params.
- Bearer Token: Sends a bearer token value as a base64-encoded string in the request's Authorization header. If you are using OIDC protocol to log in to your instance, you can use the access token of the logged-in user as a bearer token.
Use self-signed certificate
When enabled, you can upload your own self-signed certificate for accessing your endpoint. These can be useful for accessing your API without relying on external agnecies to issue certificates for authenticating the origin of your requests.
This information needs to be provided in .PEM (Privacy Enhanced Mail) format. The certificate information is stored securely in an encrypted format in the database.
Queries
Once you have set up your Authenticated API datasource, you're ready to create queries.
Visit the REST API docs to learn about the query configuration parameters.
Troubleshooting
If you are experiencing difficulties, you can refer to the Datasource troubleshooting guide or contact the support team using the chat widget at the bottom right of this page.
